New Delhi: The intelligence fusion and strategic operations (IFSO) unit of the Delhi Police Special Cell has busted a “multi-component module” involved in cheating. The police have arrested 12 people in the case so far, including the alleged mastermind, Mohammed Ansari, who was based in Jamtara, Jharkhand, a city that in recent years has emerged as a hub of cyber crime.
According to the police, the gang has cheated more than 1,000 people across the country.
K.P.S. Malhotra, deputy commissioner of police (DCP), IFSO, said, “Raids were conducted across Bengaluru, West Bengal and Jharkhand, where these modules were spread.”
The police have seized 26 phones, one laptop, 156 SIM cards, and 111 ATM cards from the accused, and frozen 111 bank accounts during the course of investigation.
“The gang has been functional for over a year. More arrests are likely,” a senior police officer said.
The matter came to light after a complaint was filed with the Delhi Police in July this year. The complainant said he was cheated after he rang a phone number to make a cheque-related query. The number was listed on Google as a customer service number for Canara Bank. Following this, he found that Rs 27.10 lakh had been transferred from his bank account to eight other accounts.
“The technical investigation and human intelligence found that this module is operating at a pan-India level. The first raid was conducted in September 2021 and six accused persons (all residents of Jamtara) were arrested from Bengaluru,” said Malhotra.
Also read: Child sex racket busted by CBI ‘extends from Pakistan to US, shares videos on social media’
The modules
According to the Delhi Police, Ansari ran the modules from Jamtara and was arrested following raids in West Bengal and Bengaluru.
“Ansari was running this multi-component module from Jamtara and would instruct those in other states about future victims. He kept in touch with the other modules, but there aren’t any layers of communication between the modules themselves,” the senior officer said.
Sources in the Delhi Police said the way raids in Bengaluru led to the arrest of members of the Jamtara module is “indicative that these people have been shifting bases to other places in the country.”
Malhotra said, “The accused created fake websites and promoted the same through engine optimisation, and also used to flash fraudulent customer care numbers. These websites would steer the victim towards the installation of applications or malware. After gaining access to the victim’s phone, they could get access to one-time passwords (OTPs) — even internet banking OTPs — and transfer large sums of money into their own accounts when the victim was asleep.”
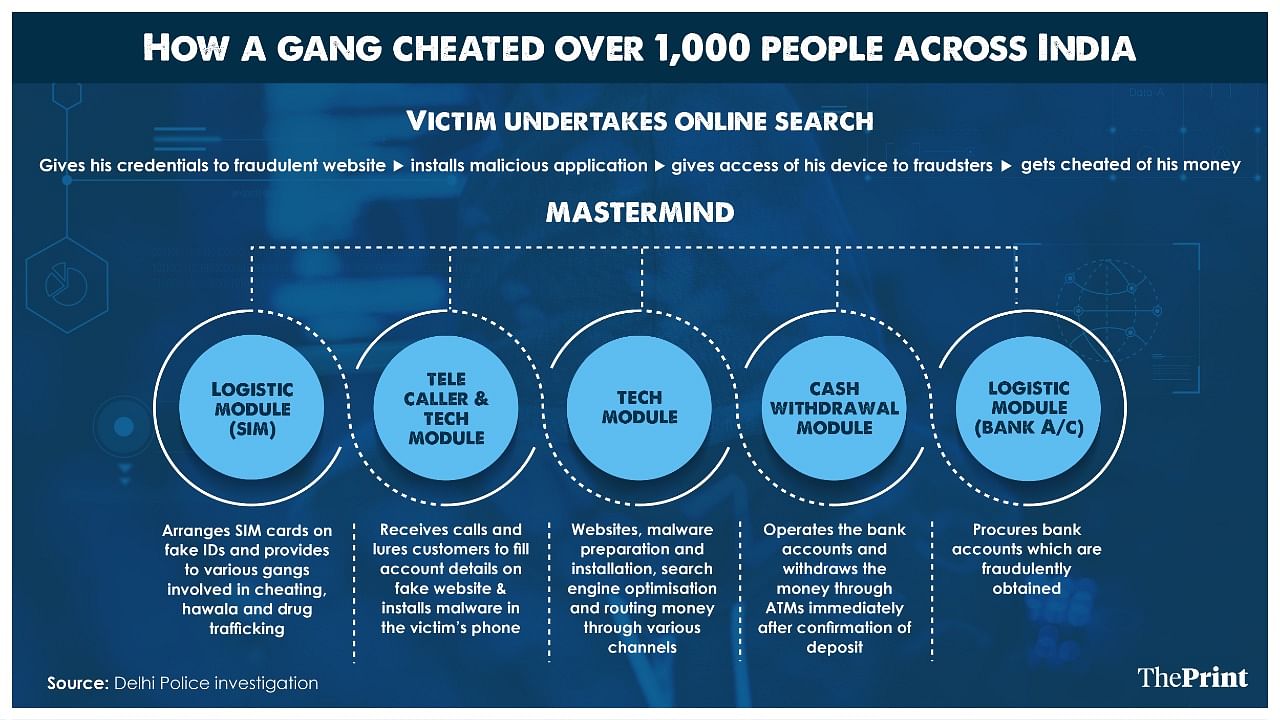
Further explaining how the nexus functioned, the senior police officer quoted above said, “Five modules operated under this nexus. The logistic module arranged SIM cards and provided them to various gangs involved in cheating, hawala and drug trafficking. The tele-caller and tech module received calls and lured the customers to fill the account details on the fake websites.”
“The tech module was responsible for these fake websites, malware, search engine optimisation and routing the money through various channels. The cash withdrawal module operates the bank accounts and withdraws the money through ATMs immediately after confirmation of the deposit. The logistic module procured fraudulent bank accounts,” added the officer.
“The West Bengal module was the logistical service provider, responsible for arranging SIM cards on fake IDs and bank accounts for the offence. The Bengaluru model was responsible for the technical operations,” said Malhotra.
(Edited by Rohan Manoj)
Also read: Target on Stripchat, get sex videos: How Ghaziabad couple ‘extorted’ Rs 20 cr in over a year



