New Delhi: The high-profile ransomware attack on Delhi’s All-India Institute of Medical Sciences (AIIMS) last month drew attention to holes in the country’s cybersecurity infrastructure, but it was hardly an isolated incident.
Industry data shows that 2022 has been the worst year so far for India when it comes to cyberattacks — a problem that has only grown with increasing digitalisation. The question now is, what next?
According to a study released Tuesday by Indusface, a Tata Capital-funded software-as-a-service (SaaS) security firm, India has become one of the most attacked and breached countries in the world. Among the 829 million cyber-attacks detected and blocked globally by the firm in the fourth quarter of 2022, close to 59 per cent were directed towards India.
“Ransomware attacks in India have increased significantly and one of the most distinguishing aspects in 2022 was the involvement of state actors,” Sameer Patil, senior fellow at Observer Research Foundation (ORF), a multi-disciplinary think-tank, told ThePrint.
“So, it is not just profit motivation. We saw how police personnel had come out with Chinese links [in AIIMS cyberattack], of how they had a role to play,” he added.
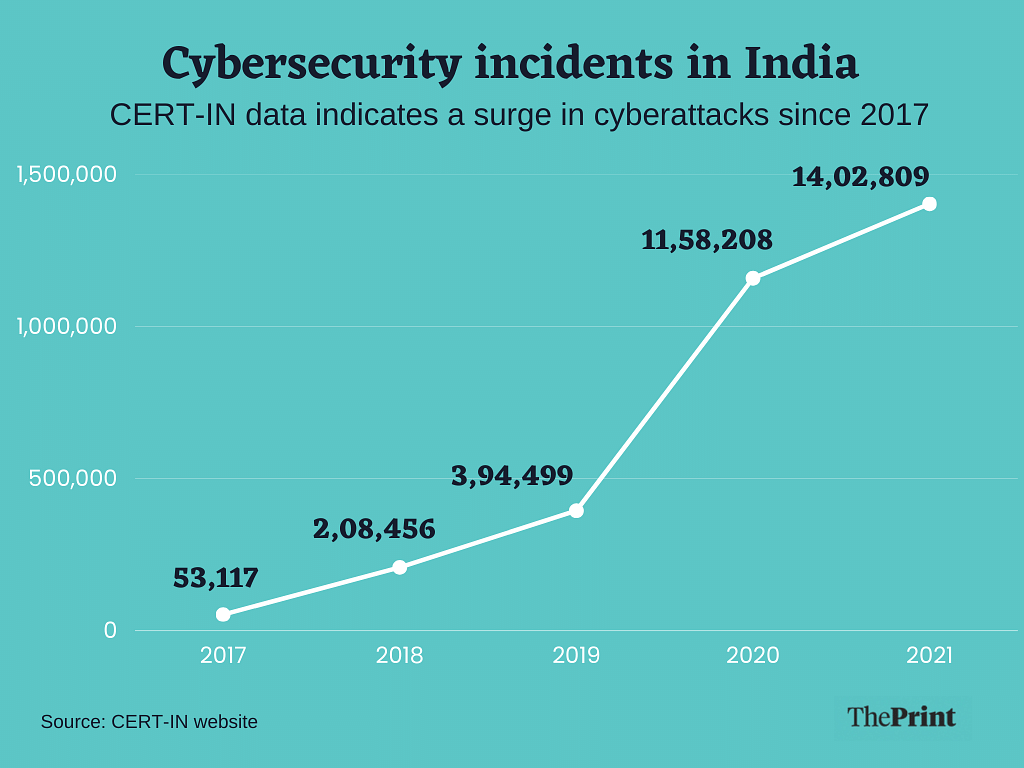
Government data, collated by the Ministry of Electronics and Information Technology’s Indian Computer Emergency Response Team (CERT-In), is available only till 2021, but that too shows an increase in cyberattacks in India.
In 2019, CERT-In handled close to 3,94,499 incidents in total, in which it suggested remedial measures for organisations and shared notes on “cyber threats and vulnerabilities”. In the same year, CERT-In issued 204 security alerts and 38 advisories.
The number of incidents handled by CERT-In surged in 2020 to 11,58,208, a near-tripling over the previous year. This surge continued in 2021, which saw 14,02,809 incidents, a 21 per cent increase.
The matters CERT-In looks into include website intrusion and malware propagation, malicious code, phishing, distributed denial-of-service (DDoS) attacks, website defacements, unauthorised network scanning or probing activities, ransomware attacks, data breaches and vulnerable services.
In this backdrop, what will the government and companies do differently in the coming year?
As the government readies its legislation on cybersecurity, numerous industry-wide surveys and sector experts say that 2023 will see companies spending significant amounts to secure their digital systems from attacks.
CERT-In has also laid out a standard operating procedure for data breaches wherein companies and other organisations are supposed to inform the government of any breach within six hours, although this move has received a mixed reaction since compliance may be challenging.
Also Read: We are in the middle of a ‘cyber pandemic’. Digital security standards need reinforcing
What will companies do differently?
A significant increase in cybersecurity budgets, the advent of a slew of cybersecurity guidelines for companies, and awareness programmes for the public by law enforcement agencies are some of the preventive methods that will be seen more in 2023.
According to Sajan Paul, managing director & country manager, India & SAARC, Juniper Networks, there will be a significant increase in cybersecurity budgets in 2023 within organisations, and a more preventive approach will be embraced.
“With the ongoing threat of cyberattacks, data security remains a major priority,” he said, citing figures from PwC’s annual Global Digital Trust Insights survey. “Over 82 per cent of business executives in India foresee an increase in their cybersecurity budget in 2023. The survey also reported that 65 per cent of business executives believe cyber criminals will significantly affect their organisation in 2023, more than in 2022,” he explained.
He added that a “zero trust” policy will be an “essential security strategy” for India, going forward.
“‘Zero trust’ is the essential security strategy in today’s hybrid work environment. Instead of assuming that everything behind the corporate firewall is safe, the ‘zero trust’ model assumes breach and verifies each request as though it originates from an open network,” Paul explained.
“Regardless of where the request originates from or what resource it accesses, ‘zero trust’ teaches us to ‘never trust, always verify’. The zero trust network reduces the complexity of securing your assets and makes it much easier to isolate problems,” he added.
Even at an individual level, experts have pointed out, there must be an increase in cyber hygiene so that people don’t inadvertently enable breaches to take place.
According to ORF’s Patil, lack of awareness about cyber-hygiene in the general populace, remains a challenge. “People don’t know what to click on and what not to in the digital space, and inadvertently become enablers [of breaches],” he said.
“Online tools like deepfake have proven themselves useful for recreating videos and content that may spread incorrect information to the public. These may have huge national security implications if not identified immediately,” he added.
Data protection Bill and CERT-In rules
India’s IT ministry has come up with the Digital Personal Data Protection Bill, 2022, defining some roles of data fiduciaries and introducing appellate committees that will deal with redressals and grievances. Many have termed it a “step in the right direction” to ensure data security.
The draft law, alongside CERT-In rules, has been part of core policy discussions in India. As mentioned earlier, the rules now require companies to report cybersecurity incidents within six hours. While this seems stringent, it might not be practical, some experts believe.
According to Akash Karmakar, partner with the Law Offices of Panag & Babu, and who leads its fintech and regulatory advisory practice, the CERT-In rules should have been subject to change as companies may not have the financial bandwidth to recognise breaches.
“The CERT-In directions mandating reporting of cyber security incidents [within six hours] was perhaps the most significant development in the cybersecurity domain this year. I’m surprised this has not been challenged since it is onerous to comply with and operationally very difficult to implement. The tightest global equivalent for reporting cybersecurity incidents is 72 hours,” Karmakar told ThePrint.
He also highlighted how the way forward could be the prescription of a “cybersecurity insurance”. This, according to him, could “go a long way”.
“The other challenge is how monetary loss owing to a cybersecurity incident is remediated. Mandating cybersecurity insurance for certain key risks, akin to a mandated motor vehicle or travel insurance, would go a long way to ensure that impacted entities are in a position to pay out compensation for personal data that is lost,” he said.
(Edited by Nida Fatima Siddiqui)
Update: The quote about cyber-hygiene has now been correctly attributed to Sameer Patil of ORF.
Also Read: New cybersecurity rules vital but still a burden, MSMEs say as govt considers extending deadline



