New Delhi: The Gujarat Police along with Military Intelligence (MI) has busted an espionage racket run by Pakistan’s Inter-Services Intelligence (ISI), which targeted defence personnel with children enrolled at Army public schools across the country, ThePrint has learnt.
Sources in the defence and security establishment said those part of the racket exploited a loophole in a website defence personnel used to pay their children’s school fees to glean information on targets.
Around the third week of July, sources added, MI officials detected a nefarious campaign by a Pakistani Intelligence Operative (PIO) using a WhatsApp number (90xxxx6792) to compromise Android mobile handsets of serving defence personnel, mostly those with wards studying in different Army Public Schools (APS) across the country.
This was done by luring them to install malicious Android applications (“.apk” files), mostly under the garb of a campaign named “Har Ghar Tiranga”, just before Independence Day.
The WhatsApp user — posing as an Army Public School official — sent a link for the malicious application to targets with a text message encouraging them to install the application and upload their ward’s photo with the tricolour to participate in the competition.
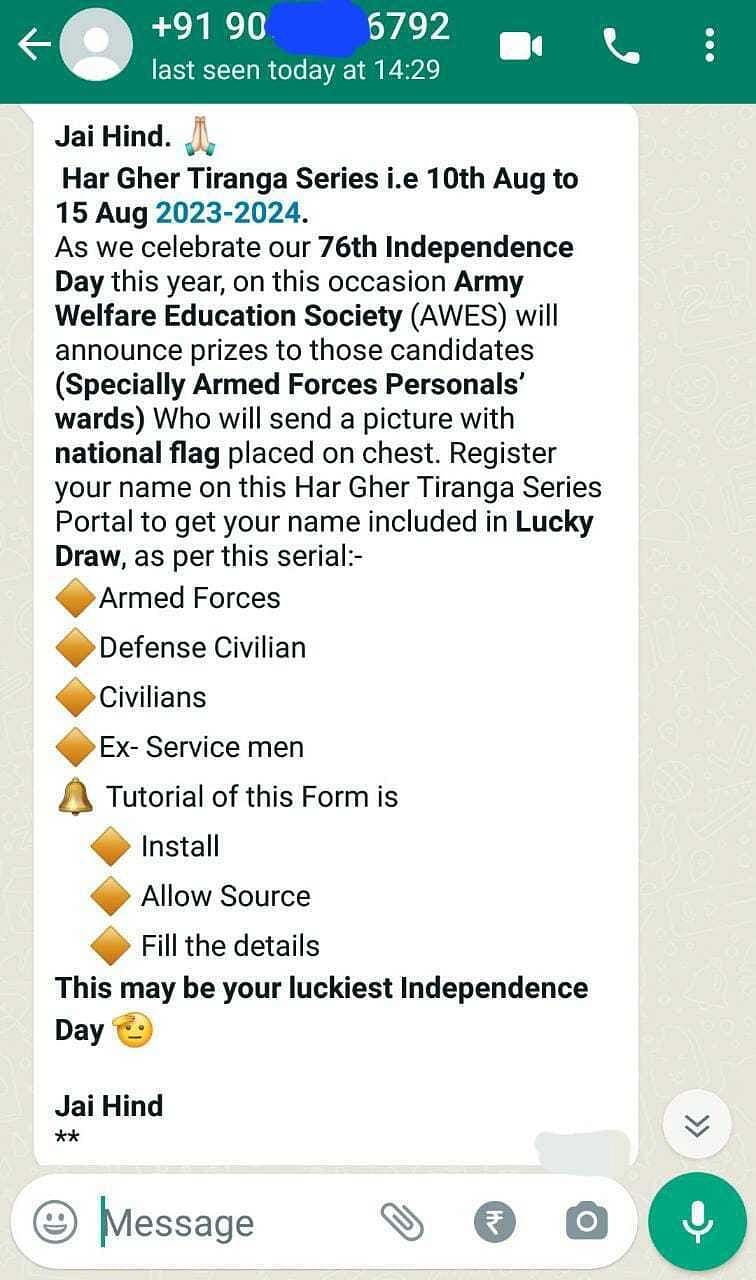
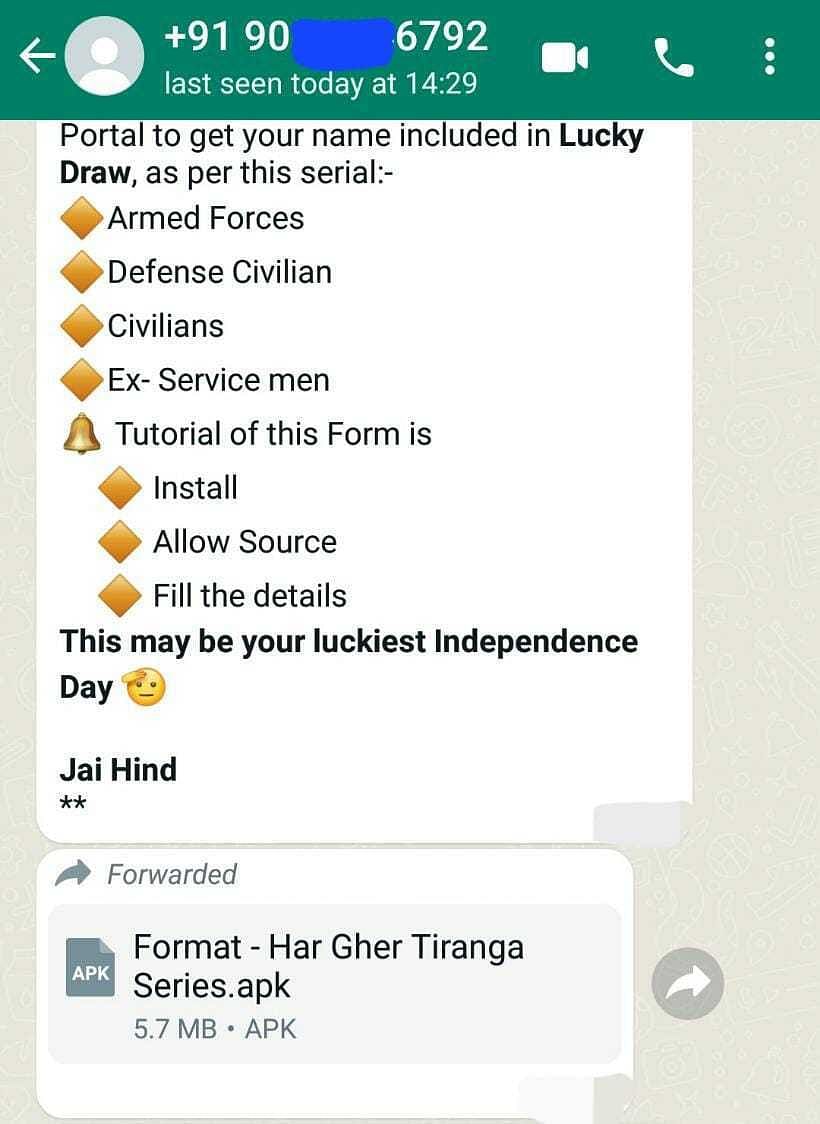
During their probe into the matter, MI officials traced the last cellular use of the mobile number in question to Gujarat and sought the assistance of the Gujarat Police Anti-Terrorism Squad (ATS).
After technical analysis and groundwork by ATS, one Labhsankar Maheshwari (53) was identified as the prime suspect for having allegedly facilitated ISI’s acquisition of the Indian mobile number by forwarding the OTP used to create a WhatsApp account for it to the Pakistani agency.
Meanwhile, with assistance from the Directorate of Air Intelligence — IAF’s intelligence arm — one such targeted Android device was accurately identified and brought in by the ATS for cyber forensics examination.
After the device was analysed by the Forensic Science Laboratory (FSL), Gujarat, it was evident that the WhatsApp number being used from Pakistan was targeting and hacking mobile devices belonging to Indian defence personnel to acquire critical information, sources added.
On Wednesday, the ATS lodged an FIR invoking suitable sections of the IPC and the IT act against the prime suspect, Labhsankar Maheshwari, at the ATS police station in Ahmedabad. He was arrested Thursday from his house in Tarapur in Gujarat’s Anand district.
Maheswari was originally a Pakistani Hindu who migrated to India in 1999 with his wife on the pretext of her fertility treatment, it is learnt.
Sources said he was initially staying with his in-laws in Tarapur who had migrated to India earlier. He kept applying for a long-term visa and with support from his in-laws established himself as a successful businessman with a grocery store, rented shops/stores and a house of his own in Tarapur. The couple did not, however, have any children.
They were granted Indian citizenship in 2006, sources said, adding that Maheshwari visited his parents in Pakistan in early 2022. Investigators suspect he was cultivated by the ISI during this month-and-a-half-long visit to Pakistan where he stayed at his parent’s house.
(Edited by Amrtansh Arora)



