New Delhi: Hackers’ groups from China and North Korea have been found to be planning to set up fake websites impersonating India’s CoWIN portal meant for people to register for vaccination, according to cyber intelligence firm Cyfirma.
The firm said while the Chinese group is currently silent on the plans, the North Korean hackers discussed CoWIN on dark web as recently as on 30 March.
The purpose of these fake CoWIN sites is to “to collect personal information” from unsuspecting Indian users and use that “for further cyberattacks”, Cyfirma said in its report, accessed by ThePrint.
According to the company, both the Chinese and the North Korean hackers are state-linked or state-backed.
It was Cyfirma that had alerted about Chinese hacker group Stone Panda targeting IT infrastructure of Indian vaccine makers Bharat Biotech and Serum Institute of India (SII) in the beginning of this month, according to a Reuters report.
Speaking to ThePrint, Cyfirma CEO Kumar Ritesh told ThePrint last week Chinese state-linked hacker group known among cybersecurity professionals as ‘Stone Panda’ were found to be “discussing” as of 14 March malicious IP addresses from which fresh attacks could be launched on the likes of SII and Bharat Biotech. However, he also said, “…by now the target might have changed…it might be somebody else”.
Ritesh said there is no further update with him on this to share.
The Reuters report had said SII and Bharat Biotech declined to comment on this, while the Ministry of Information Technology’s Indian Computer Emergency Response Team (Cert-In) said the matter was being looked into by its operations director, S.S. Sarma.
Cyfirma said it had alerted Cert-In about the Chinese hackers.
The cyber intelligence firm has offices in Singapore and Japan, and CEO Kumar Ritesh is based in Singapore. He told ThePrint he had previously worked with MI6, the United Kingdom’s secret intelligence service, for nearly nine years as its cyberwarfare unit head.
Also read: China’s cyberattack on Maharashtra power grid was to improve PLA’s bargaining position
Fake CoWIN sites
Ritesh described instances when Cyfirma observed that state-backed North Korean hacker groups were discussing on dark web forums the creation of fake CoWIN sites to collect personal data from Indian users.
He, however, said Cyfirma has not yet witnessed the hacking plans being put into action.
“We call ourselves a predictive intelligence provider, because some of these acts haven’t happened. It is not an incident just yet. This is being planned by cybercriminals,” Ritesh said.
Cyfirma observed the latest discussion by North Korean hackers to set up fake CoWIN sites started on 14 March and continued as on 30 March.
The firm shared a list of malicious domains (see chart) that it believes the Korean-speaking hackers were planning to set up to impersonate the original CoWIN portal.
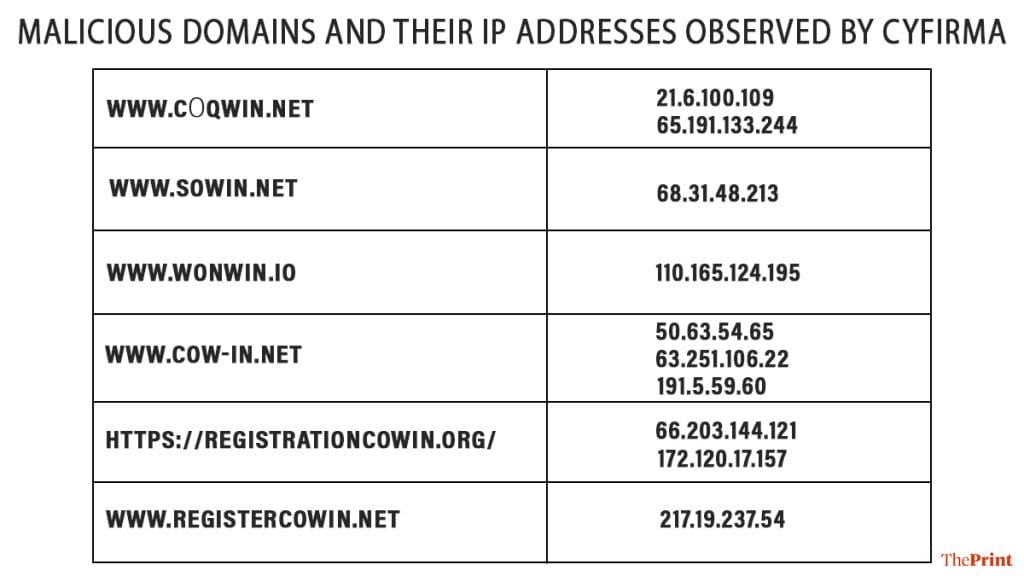
Giving details about the North Korean hackers’ possible “plan” after creating the fake sites, Ritesh said they could then send phishing emails containing links to these malicious sites to the users in India. Unwitting users who would think it to be a genuine email would reach the fake website and try to register for a Covid vaccine by providing personal details such as phone number and Aadhaar or PAN details through which hackers can collect that data, Ritesh explained.
Hackers usually gain access to email addresses from email databases made available on the dark web after they are collected from other hacking activities.
ThePrint reached Ram Sewak Sharma, chairman of the CoWIN panel, through WhatsApp for a comment on the matter but he did not reply. An email sent to a helpline ID on the health ministry website elicited only an automated response that acknowledged the mail.
Chinese hackers
Prior to the North Korean hackers, it had been a Chinese group that was found to be discussing creation of fake CoWIN sites for the same purpose of collecting India users’ personal data.
Ritesh said Chinese hackers have gone quiet on the plans, and it is possible that the North Korean hackers are being paid by another country to carry it out.
It is unusual and “quite alarming to see” but there has been a rise in collaboration between state-sponsored hackers of different countries since mid-2019, Ritesh said.
Cyfirma had observed two instances involving Chinese hackers. The first was on 1-2 March, and it was linked to state-backed hacker group ‘Gothic Panda’. Cyfirma observed the hackers had named the campaign “Unlshed21”.
The second instance was observed between 11 and 16 March. Cyfirma said these were Mandarin-speaking Chinese hackers but could not be clearly linked to Gothic Panda.
The Chinese hackers aimed to collect personal information in the same method as the North Koreans — by sending phishing emails.
Some of the fake site names the Chinese hackers had been discussing were ‘http://c0vi19.net’, ‘https://selfregistration.covin.org’, and ‘https://selfregistration.covin.io’.
IP addresses to conduct such malicious activity can be purchased on the dark web, according to Ritesh. The IP addresses noted in all three instances were traced to countries such as Mexico, Russia, South Korea, India, and China.
Cyfirma said they alerted Cert-In about the Chinese hacker-related instances twice on 1 and 2 March, but yet to do that with regard to the North Korean group.
ThePrint had reached Cert-In via email on 11 March to ask about the incidents related to the Chinese hackers, but received no response.
(Edited by Sanghamitra Mazumdar)
Also read: China, Russia & North Korea hackers target AIIMS, SII, Patanjali for Covid data — report







North Korea is begger country depending our Weat and rice exports now on attacking on us ?
Shame on North Korean beggar people